Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Cloud Computing: Detection and Prevention of DDos Attacks Influencing the Adoption of Cloud Computing to the Small and Medium Enterprises in the Sri Lankan Business Context
Authors: Madusha Dalugama
DOI Link: https://doi.org/10.22214/ijraset.2024.65959
Certificate: View Certificate
Abstract
Cloud computing can be categorized as one of the most exciting technologies available due to the flexibility and the low-cost adaptability for the small and medium enterprises (SMEs). There are many advantages of moving SMEs to cloud such as business reputation, enhancing of the SMEs are some of them, but SMEs are slow to adopt them due to privacy concerns, security concerns and lack of cyber security knowledge. The purpose of this paper is to identify the Distributed Denial of Service attacks which is affecting the Sri Lankan SMEs when adopting to the cloud computing. This paper discusses about the three detection and prevention mechanism of the DDoS attacks it includes Pall Based detection, flow-based detection and Anomalies and frequency-based detection methods. Moreover, prevention mechanisms include preventing using machine learning, preventing using Neural Network and Deep Learning. Further this paper discuss why Sri Lanka is far behind the technology and what are the main factors affect for the SMEs face when adopting to the clod environment. Further this paper elaborates the impacts, latest tools, and technologies available for mitigation, data security and privacy concerns, legal issues, and standards available for the SMEs when adopting to the cloud environment.
Introduction
I. INTRODUCTION
The way organizations run is changing due to the fast-developing technology known as cloud computing. A shared pool of computer resources, including servers, storage, applications, and services, may be easily and instantly accessed using this paradigm over the Internet. Many companies are adopting the cloud computing modal because of its scalability, efficiency, and flexibility. Yet, there are worries about cloud computing's security, especially in the distributed denial-of-service (DDoS) attacks. This paper will discuss how DDoS attacks affect Sri Lankan SMEs when adopting to the cloud environment[1].
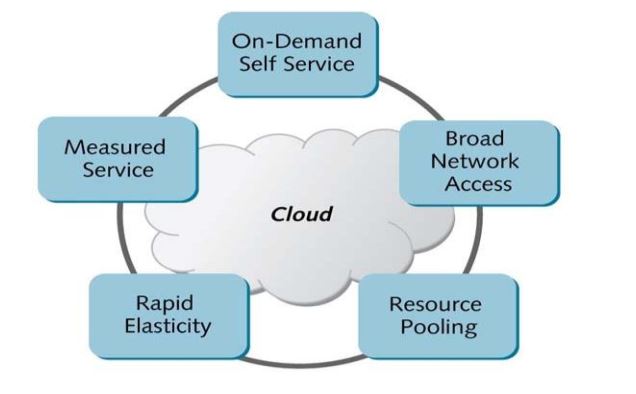
Fig 1: Essential Characters of the Cloud Computing [4]
When investigating cloud platforms, it gives access to the users to share the information whenever they need it. There is a large amount of data available, and they are allocated among the users. Today it has become a new challenge to protect the data which is stored in the cloud from various types of attacks.
According to the [2],[3] these papers will elaborate security issues related to the cloud computing. In that DDos attacks is a serious type of attacks this is happen by flooding network packets into a single host.
Although, these measures, SME in Sri Lanka remain a question when adopting to the cloud computing due to the heavy risk of DDoS attacks. This factor has led to the slow adoption of cloud computing in the SMEs. To overcome these issues cloud service providers has to educate all the SMEs regarding the security measures they have to adopt to prevent DDoS attacks.
DDoS Attacks: A distributed denial of service attack (DDoS) is a malicious attempt to obstruct a website, server, or network from operating normally by flooding it with traffic from several sources. DDoS attacks are one of the most significant security risks to cloud computing platforms. DDoS attacks can cause business reputational harm, downtime, and economic losses. SMEs are especially at risk of DDoS attacks because of their constrained resources and lack of cybersecurity knowledge.[4]
This paper will discuss how to mitigate the DDoS attacks which are vulnerable for SMEs when moving to cloud environment. Objective of this paper is to identify the correct mechanism to implement is Sri Lankan SMEs in order to mitigate the DDoS attacks and designing a cloud security strategy for SMEs to detect and prevent DDoS attacks.
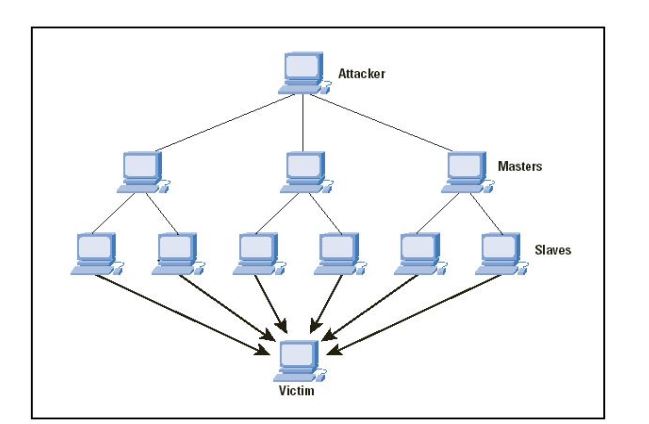
Fig 2: Typical DDoS Attack [4]
II. LITERATURE REVIEW
To provide universal network access to computing resources. Furthermore, cloud computing provides more benefits to the MSEs such as good efficiency, flexibility, and the cost is low compared with others. With that SMEs can improve their productivity and enhance their business to the world. As per [5] DDoS attacks can be elaborate as the attacks which attempts to disturb the function of the website. Further this can be a most significant threat to the SMEs cloud system. DDoS may damage the business reputation, can loss the revenue. Most of the SMEs are attacked since they are having a lack of cyber security knowledge.
Cloud computing will lead enterprises to run their application in a well manner with a better utilization of the resources and less maintenance, and that will enable to increase the demand of the business. Cloud computing will reduce the cost of the initial investment. Adoption of the cloud computing will lead to many advantages in SMEs as they are using automatic software updates, controlling of documents, security and disaster recovery.[6]
With the experience of the organization getting engaged with the cloud platform they start to shift the core business ideas to the cloud. In terms it will be more complex when it comes to data management, and system manage with multiple cloud vendors. There are different types of vendors who delivered cloud platforms such as Software as a service (SaaS), Platform as a service (PaaS) and Infrastructure as a Service (IaaS). [7]
In the past years adoption of cloud computing was slower due to many reasons such as bandwidth, mobility and fear of losing the data, security issues, attacks, and mainly unawareness [8]. When a SME is moved to a cloud environment it is enormous, and benefits will vary when comparing with the companies those who have cloud and those don’t.
A. Challenges of Cloud Computing Adoption
Overall cloud computing has faced many outgoing rejections [9]. There are technical and organizational obstacles which can prevent SMEs from adapting to cloud computing. Security is the main principle. An IDC report stated that 75% of the persons who owns the SMEs stated that security is the first concern is while moving to cloud computing environment [10]
The second concern is related to the lack of support from the top management since cloud computing required knowledge and skills to implement the services. [11]
Third concern is the trust between cloud service providers and between the SMEs. It’s because the cloud service providers are not available for when there is a security or data breach is happened. [11]
A study which was carried out by the Eastern province in Sri Lanka states [12] that 36% of the SMEs are no longer agree to moving their business to the cloud computing. The reason behind that is as follows.
- Technology Issues include computer literacy.
- Security Issues.
- Top Management issues
- Size of the Market
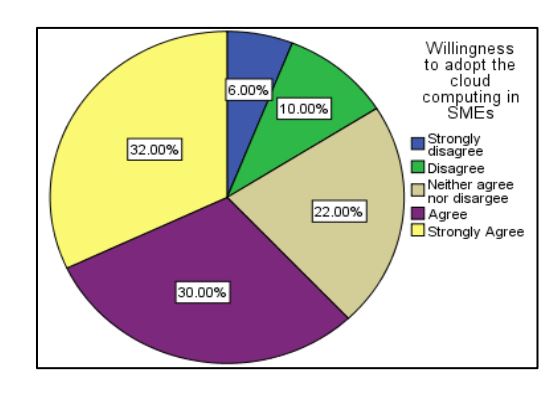
Fig 3: Adoption of Cloud Computing [14]
B. DDoS Attacks Influencing Adoption of Cloud Computing in Sri Lanka
Sri Lanka is a country which is currently known as under developing country and SMEs are the backbone of the economy of the country. As per [13] 75% of the market is hold by the SMEs and among that 55% of the Gross Domestic Product (GDP) is contributed by the SMEs. In Sri Lankan Context SMEs are facing number of DDoS attacks and it is increasing day by day. This will result in the loss of revenue, disruption of the business operation and overall damage to the business’s reputation.
DDoS attack affected from business moving to cloud in Sri Lanka. Since due to the perceived security risks and they fear that their data will be compromised and that will directly reflect to their business. [6]
Moreover, due to the increased cost of adapting to the cloud environment, may cause additional invest due to security measures and mainly on DDoS attacks. This will include all the hardware and software. Further, DDoS attacks resulted in lack of trust among the SMEs due to the cloud providers do not maintaining the service properly. As per the [12] SMEs are fear to adopting to the cloud environment with the risk of DDoS attacks. This has resulted in a disadvantage when compared with the large companies.
DDoS mainly focuses on high quality IP packets in a specific network. In SMEs when the cloud is shared information with the large number of clients DDoS attacks have the capability to attack. Most of the SMEs available in Sri Lanka cannot protect against the DDoS attacks. It’s because they cannot stop the network traffics[14]. On some occasions it is possible with the Intrusion Prevention System (IPS) but there should be a pre-defined signature to act against DDoS attacks. Unfortunately, like IPS when there is a firewall attacker might send legitimate traffics where firewall couldn’t be able to identify that also lead to a failure.
Since DDoS attacks are the most powerful attacks among all the SMEs in Sri Lanka cannot be identify them, it is because of lack of cyber security knowledge. In 2018-2022 as per the CERT report [15] Sri Lankan SMEs getting continues attacks which will lead to steal every information. This will lead to a lack of trust among the customers and that will lead to harming the business reputation. In that occasion all the SMEs which are in rural areas are lacking behind in moving to cloud computing.
III. METHODOLOGY
This paper will discuss the Methodology which adopted when mitigating DDoS attacks which influence moving of SMEs to cloud environment. In that there are 03 Methods will be discussed on how to Detect the DDoS attack and how prevent the DDoS attacks which is influencing for the moving to Cloud Computing by SMEs. The following are the methodology adopted.
1) Detection Methods
- Poll-based monitoring and detection.
- Flow-based Network Parameter Detection.
- Anomalies and Frequency based detection.
2) Prevention Methods
- Preventing DDoS Using Machine Learning
- Preventing DDoS using Neural Networks
- DDoS prevention using Deep Learning
A. Detection of DDoS Attacks Influencing SMEs
1) Poll-Based Monitoring and Detection Method
As per [5] we can detect DDoS attacks is to examine the detection strategy and the current reporting capabilities. In that Simple Network Management Protocol (SNMP) is standard protocol which is used to determine information about network devices. This can be used in every router, switches, servers etc. Further SNMP can revolve information such as structure interfaces, High CPU, High packets generated per second, high packets losses per second. Generally, when the device is under DDoS attack there can be a greater deviation among the metric when comparing with the normal range.
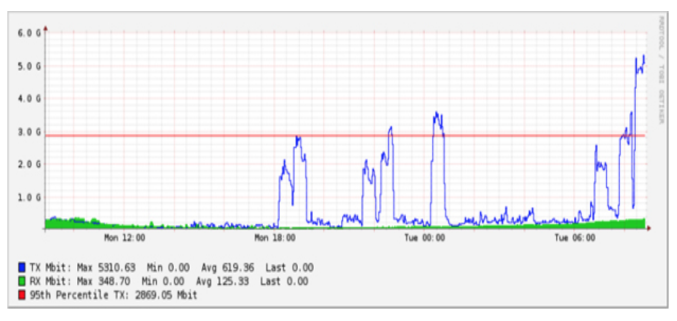
Fig 4: Bandwidth Spike [7]
2) Flow-Base Network Parameter Detection
This was a mechanism which was introduced by CISCO, and this is a push-based network detection methodology. Information about the device is collected by itself and sent to the collector. Information which is collected will be pushed to the collector and it is a centralized collection point for exporters. Some of the flow based vendors are JFlow, NetFlow [5]
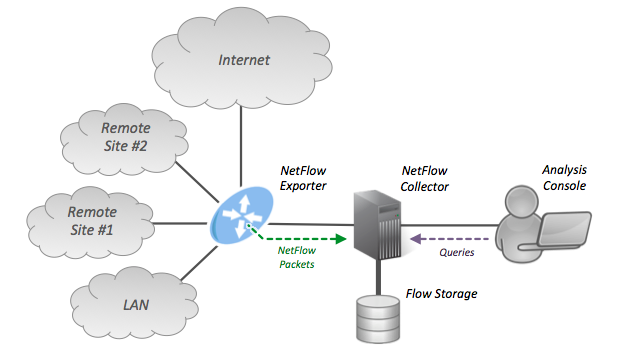
Fig 5: NetFlow Architecture [7]
3) Anomalies and frequency-based detection
Anomaly and frequency-based detection are commonly used as a combination method since it will effectively detect DDoS attacks. Anomaly is based on identifying patterns which occurs significantly from an unexpectable behavior and frequency based detection will identify patterns occurring more frequently thank the expectation.[5]
B. Prevention Mechanism for DDoS Attacks Influencing SMEs
1) DDoS prevention using Machine Learning
To prevent the SMEs from DDoS attacks which will affect cloud computing the following mechanisms can be obtained. First this mechanism identify the abnormal traffic within the network. Then the mechanism will be triggered to prevent DDoS attacks. These mechanisms can be implement and applied using various algorithms of AI, neural network, IoT, and machine learning [16]
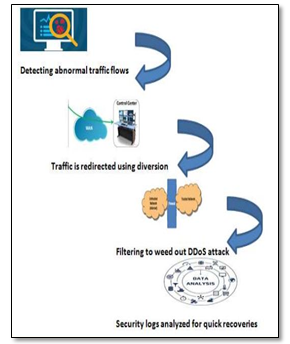
Fig 6: DDoS Prevention Mechanism [18]
By using C.4.5 Algorithm DDoS attacks can be handled easily and effectively. When there is a incoming flooded traffic then there will be an immediate respond and traffic will be analyzed by a trigger and in an instant preventive action will be taken immediately. Decision Tree will be utilized to various signatures to analyze the traffic [16],[17].
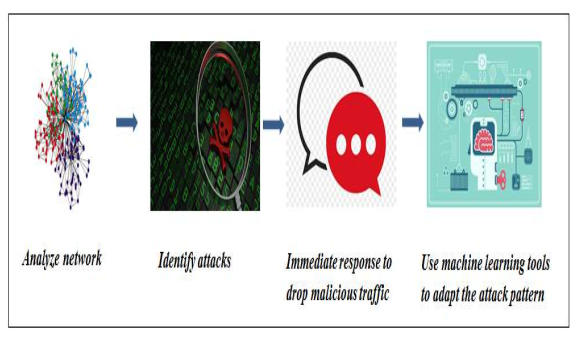
Fig 7: How DDoS prevent using Machine Learning [19]
2) DDoS Prevention using Neural Network
Using Neyman Person Cost Minimization Strategy and Resilient Back Propagation, DDoS attacks can be. There should be a preprocessed data set and that dataset will be identified by the neural network and that will lead to capture DDoS attacks and has a low false notification rate. [18]
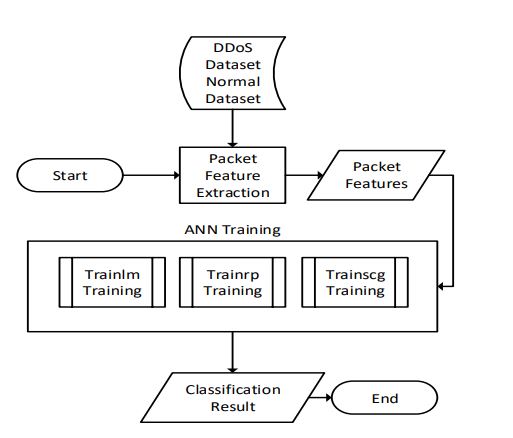
Fig 8: Neural Network Packet Classification [20]
3) DDoS Prevention using Deep Learning
Deep learning can be used to mitigate DDoS attacks by using a Deep Defense Strategy. In here new pattern and rules will be designed to capture the abnormal traffic by using 02 datasets. This include Normal data set and abnormal dataset and will be input for the deep learning algorithm to classify them. Afterwards classification labels will be assigned to each dataset and will be used as prevention method to be used for DDoS attacks. [16]
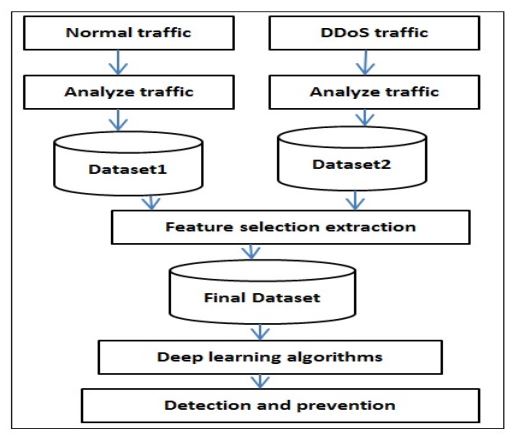
Fig 9: DDoS Prevention using Deep Learning [17]
IV. MPLEMENTATION PROCEDURE
To implement the methodology which was identifies to detect and prevent DDoS attacks ADDIE methodology will be used and that will build the confidentiality towards the SMEs in Sri Lanka to move to the Cloud Computing environment. In implementation stage 05 phases will be carried out. Following are the 05 phases of ADDIE methodology [19].
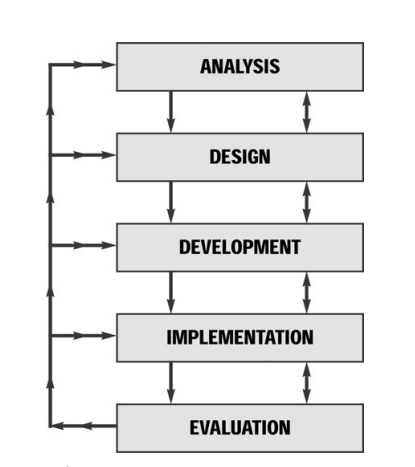
Fig 10: ADDIE Methodology [19]
- Analysis: Initial analysis will be carried out by the network specialist and management of SMEs. This will lead to a discussion of the problems and goals.
- Design: In the second stage Design of the mechanism will be done and will be done as per the requirement of the SMEs.
- Development: In this stage designed methodology will be developed. In that all the resources mitigating technologies will be adopted.
- Implementation: Implementation of the development will be carried out in this stage. User satisfaction and the mitigation strategies will be tested in this stage.
- Evaluation: Management of the SMEs will evaluate the process to check whether they have met the requirements. Evaluation will take place in around 3 months.
This ADDIE methodology can be utilized in SMEs when building a mechanism to adoption of cloud computing and mitigation of DDoS attacks. Careful and proper planning must be adhered to when implementing this. Since Sri Lanka is a developing country and have low knowledge of Cyber security and cloud computing they must have to have a proper understand about the technologies used
V. SECURITY AND PRIVACY CONCERNS
Data security refers to the Confidentiality, Integrity, Availability (CIA). Further data security is very crucial for the customers who use cloud computing. According to [20] improved data security is playing a vital role in the cloud environment. Data security breaches can cause greater damage to the business environment and for reputation which cannot be reclaimed. In Sri Lanka Information technology Act no 19 of 2006 will protect all the customers from data security and privacy concerns [21]. Through a DDoS attack data security can be breached and mitigation techniques should be taken to protect the customer data. Since the SMEs have little knowledge about the procedures it will raise a potential security threat and it is a way of information leakage.
Data privacy concerns the sensitive data which is available in the cloud. This can be all the information about the customers, including their personal details and the credit card information. Privacy is one of the core components in the cloud computing and issues with the SMEs are that lack of transparency and poor trustworthiness, In the cloud environment in SMEs data stored mut be kept in a secure manner and should be prevent from theft and unauthorized sharing. [1]
VI. CLOUD SECURITY STANDARDS
As per the CERT Sri Lanka [22] cloud security standard refers how the SMEs should adopt to the standards after migrating to the cloud environment.
In that ISO/IEC 20000 and 27001, Cloud Security Alliances (CSA) and National Institute of Standard Technology (NIST) 800-61 are some of the key standards where SMEs should adopt when moving to the cloud environment. These policies and procedures must be included in the organization to control the legal, physical, and technical issues to manage the risks within the organization. If there is good understanding of the cloud related risk and control of the risks, and risk mitigation it will be a great benefit for the SMEs.
SMEs in Sri Lanka has a fear to get the standardization with the lack of knowledge. Most of the companies are not willing to move with foreign employees. They will only move with the local customers. As per the CCC Sri Lanka report [23] 58% of Sri Lankan SMEs do not follow the cloud security standards. This will lead to a cyber threat of their SMEs.
Moreover, cloud security standards will enable us to facilitate risk management in the cloud environment. The standards will allow to assist organization in conducting the risk management and it will implement controls to mitigate risks.
VII. LEGAL ISSUES
Wide-ranging legal issues are raised by cloud computing. As it relates to protect individuals’ information related to the personally identifiable and protecting sensitive and potentially confidential business information that is either directly accessible through or gleaned from cloud systems, there are significant issues with data privacy and security. Additionally, there are numerous contracting structures (such as licensing, service agreements, online agreements, etc.) under which cloud services may be provided to clients.[24]
Some of the main legal challenges can be arise in cloud computing are [25] [26];
- Liability Issues: In Sri Lankan context Managing levels of the SMEs are afraid of taking any liabilities to their hand since the market is not stabilized.
- Copyright Issues: Most of the data is the intellectual property of an individual or an organization. In that of there is any copywrite issues that SMEs will be imposed for legal penalties.
- Application Law Issues: Laws are different from the country wise. Means applications will follow the law of the origin country cloud will follow the US cloud act this will directly affect for the SMEs in Sri Lanka.
- Data protection: This will enable the service user and the end users. Data of a single user may be involved laws in different countries since the data stored in the cloud may include not only Sri Lanka.
- Data Portability: On some occasions due to the upgradation of the cloud will lead to a data mismatch in some instances this will happen with the issues with the standardization.
Sri Lanka finds it hard to find Cloud Service Providers (CSP) since we have intermediate personnel with Internet Service Providers (ISP). Since there is a strong requirement of the standards in cloud computing cloud service providers find some tricky solutions when dealing with the domestic laws of the country. Both nationally and internationally, there is a complex relationship between data protection laws and IT regulations. There needs to be an agreement among rich and developing countries on handling the data. Until the international community resolves the data ownership issue, the data hosted on cloud servers will be subject to legal and jurisdictional ambiguity.[26]
Conclusion
In conclusion, Detecting and preventing of DDoS attacks can be impact for the adopting for the cloud environment of the SMEs in Sri Lanka. If SMEs are available in cloud computing, it can be vulnerable for DDoS attacks. In that there is a risk of Sri Lankan persons of migrating to a cloud environment. As a result of that if there is a good mechanism for mitigating the DDoS attacks there will be trust of cloud computing and people who are with SMEs will move to the cloud-based SMEs. Since Sri Lanka is a developing country and there should be a trustworthy with CSP and SMEs. To mitigate DDoS attacks SMEs in Sri Lanka it can be use detection method with machine learning. This is done by using a decision tree and using a machine learning algorithm called C4.5 algorithm which was developed by Ross Quinlan. This is an accurate way, and this algorithm is based on ID3 or known as Iterative Dichotomiser this will find a decision tree which is generated by C4.5. The dataset is loaded into the WEKA tool and can be pretested in SMEs. DDoS attacks can be detected and prevented if there is a correct mechanism. As mentioned in the research paper we can use strategies to mitigate them. Further there are many technologies but their accuracy of preventing mechanism is questionable. The main problem in Sri Lanka is weak cyber security knowledge and lack of understand the advantages of cloud-based SMEs. There is some technology solution which can be effective and budget friendly and if the CSP can give a brief introduction with the help of government bodies SMEs can be moved to cloud environment.
References
[1] R. Nagahawatta, M. Warren, S. Lokuge, and S. Salzman, “Security Concerns Influencing the Adoption of Cloud Computing of SMEs: A Literature Review”. [2] J. Francois, I. Aib, and R. Boutaba, “FireCol: A Collaborative Protection Network for the Detection of Flooding DDoS Attacks,” IEEEACM Trans. Netw., vol. 20, no. 6, pp. 1828–1841, Dec. 2012, doi: 10.1109/TNET.2012.2194508. [3] M. H. Khalil, M. Azab, A. Elsayed, W. Sheta, M. Gabr, and A. S. Elmaghraby, “Maintaining Cloud Performance under DDOS Attacks,” Int. J. Comput. Netw. Commun., vol. 11, no. 6, pp. 1–22, Nov. 2019, doi: 10.5121/ijcnc.2019.11601. [4] P. Daffu and A. Kaur, “Mitigation of DDoS attacks in cloud computing,” in 2016 5th International Conference on Wireless Networks and Embedded Systems (WECON), Rajpura: IEEE, Oct. 2016, pp. 1–5. doi: 10.1109/WECON.2016.7993478. [5] E. Chou and R. Groves, Distributed Denial of Service (DDoS): practical detection and defense, First edition. Sebastopol, CA: O’Reilly Media, 2018. [6] T. C. Gamage, “Determinants of Cloud Computing Adoption among SMEs in Sri Lanka: A Meta Theoretical Framework,” Int. J. Asian Soc. Sci., vol. 9, no. 2, pp. 189–203, 2019, doi: 10.18488/journal.1.2019.92.189.203. [7] M. G. Avram, “Advantages and Challenges of Adopting Cloud Computing from an Enterprise Perspective,” Procedia Technol., vol. 12, pp. 529–534, 2014, doi: 10.1016/j.protcy.2013.12.525. [8] S. C. Misra and A. Mondal, “Identification of a company’s suitability for the adoption of cloud computing and modelling its corresponding Return on Investment,” Math. Comput. Model., vol. 53, no. 3–4, pp. 504–521, Feb. 2011, doi: 10.1016/j.mcm.2010.03.037. [9] E. O. Yeboah-Boateng and K. A. Essandoh, “Factors Influencing the Adoption of Cloud Computing by Small and Medium Enterprises in Developing Economies,” vol. 2, no. 4, 2014. [10] T. Mungai, “Cloud Computing in Managing Big Data,” Eur. J. Eng. Technol. Res., vol. 1, no. 6, pp. 30–33, Jul. 2018, doi: 10.24018/ejeng.2016.1.6.221. [11] H. Gangwar, H. Date, and R. Ramaswamy, “Understanding determinants of cloud computing adoption using an integrated TAM-TOE model,” J. Enterp. Inf. Manag., vol. 28, no. 1, pp. 107–130, Feb. 2015, doi: 10.1108/JEIM-08-2013-0065. [12] A. F. Nuskiya, “Factors Influencing Cloud Computing Adoption by SMEs in Eastern Region of Sri Lanka”. [13] “UN Global Compact Network Sri Lanka?» SMEs: A Boon to the Sri Lankan Economy.” https://www.ungcsl.com/?p=1454 (accessed May 05, 2023). [14] F. Sabahi, “Cloud computing security threats and responses,” in 2011 IEEE 3rd International Conference on Communication Software and Networks, Xi’an, China: IEEE, May 2011, pp. 245–249. doi: 10.1109/ICCSN.2011.6014715. [15] “Sri_Lanka_CERT_Annual_Activity_Report_2020.pdf.” [16] S. Potluri, M. Mangla, S. Satpathy, and S. N. Mohanty, “Detection and Prevention Mechanisms for DDoS Attack in Cloud Computing Environment,” in 2020 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kharagpur, India: IEEE, Jul. 2020, pp. 1–6. doi: 10.1109/ICCCNT49239.2020.9225396. [17] I. Sreeram and V. P. K. Vuppala, “HTTP flood attack detection in application layer using machine learning metrics and bio inspired bat algorithm,” Appl. Comput. Inform., vol. 15, no. 1, pp. 59–66, Jan. 2019, doi: 10.1016/j.aci.2017.10.003. [18] I. Riadi, A. Wirawan, and S. -, “Network Packet Classification using Neural Network based on Training Function and Hidden Layer Neuron Number Variation,” Int. J. Adv. Comput. Sci. Appl., vol. 8, no. 6, 2017, doi: 10.14569/IJACSA.2017.080631. [19] M. C. Nguyen, P. W. C. Prasad, A. Alsadoon, L. S. Hoe, and A. Elchouemi, “Cloud-based learning: A study on rapid learning content development with an Agile method,” in 2016 IEEE Global Engineering Education Conference (EDUCON), Abu Dhabi, United Arab Emirates: IEEE, Apr. 2016, pp. 974–979. doi: 10.1109/EDUCON.2016.7474669. [20] M. Stieninger, D. Nedbal, W. Wetzlinger, G. Wagner, and M. A. Erskine, “Impacts on the Organizational Adoption of Cloud Computing: A Reconceptualization of Influencing Factors,” Procedia Technol., vol. 16, pp. 85–93, 2014, doi: 10.1016/j.protcy.2014.10.071. [21] J. Fernando and S. Wickramasinghe, “Sri Lanka Personal Data Protection Legislation – An Overview,” SSRN Electron. J., 2022, doi: 10.2139/ssrn.4246818. [22] “Minimum_Information_Security_Standards_Version1_22-11-2021.pdf.” [23] “Chamber-of-Commerce-2021-22__web-1.pdf.” [24] J. A. Bowen, “Legal Issues in Cloud Computing,” in Cloud Computing, R. Buyya, J. Broberg, and A. Goscinski, Eds., Hoboken, NJ, USA: John Wiley & Sons, Inc., 2011, pp. 593–613. doi: 10.1002/9780470940105.ch24. [25] E. W. N. D. Bandara, K. H. Perera, and H. P. K. Madushika, “Study on the Impact of National Policy Framework on the Performance of Small and Medium Enterprises (SMEs) in Gampaha District,” SSRN Electron. J., 2020, doi: 10.2139/ssrn.3851017. [26] J. S. Saini, D. K. Saini, P. Gupta, C. S. Lamba, and G. M. Rao, “Cloud Computing: Legal Issues and Provision,” Secur. Commun. Netw., vol. 2022, pp. 1–13, Aug. 2022, doi: 10.1155/2022/2288961.
Copyright
Copyright © 2024 Madusha Dalugama. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET65959
Publish Date : 2024-12-16
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

